What are Cryptocurrency Forensics and Asset Tracing?
Cryptocurrency forensics and asset tracing are investigative methods of tracking financial transactions on the blockchain. They are used to identify perpetrators and locate assets.
The ability to identify and locate digital assets can be critical for civil litigation, criminal prosecution, bankruptcy proceedings, regulatory enforcement and judgment collection. Cryptocurrency tracing is commonly part of the investigation and recovery process for victims of online fraud, theft, hacking and extortion schemes.
Hudson Intelligence conducts cryptocurrency forensics investigations for law firms, investors, exchanges, regulators and law enforcement. Every investigation is led by a Cryptocurrency Tracing Certified Examiner (CTCE) and Certified Fraud Examiner (CFE).
How can Bitcoin and Cryptocurrency be Traced?
Many people believe cryptocurrencies are completely anonymous. Transactions for Bitcoin and other virtual currencies are publicly reported on online blockchain ledgers that identify users solely by their cryptocurrency address – a long string of letters and numbers – without names, locations, or other personally identifying details. Law enforcement agencies, regulators, and financial investigators have developed innovative methods to pierce that veil of anonymity. Blockchain intelligence tools and investigative techniques, including analysis of common spend and address reuse, can be used under certain conditions to de-anonymize cryptocurrency transactions. In response to increased scrutiny and surveillance, cybercriminals have honed their money laundering methods like layering, and adopted new privacy-enhancing technologies. The cat-and-mouse game between criminals and investigators continues to escalate across cryptocurrency markets.
What Kind of Information Can be Traced?
The twin goals of cryptocurrency forensics and asset tracing — identify the perpetrator, and find their funds — are pursued through several areas of analysis and fact-finding:
Attribution Data: Blockchain intelligence tools collect and analyze ownership attribution information for thousands of entities, which can be used to de-anonymize blockchain addresses for identification of criminals and investigative subjects. These systems rarely provide personally identifying information (PII) for individual owners of specific cryptocurrency assets, but may identify known associations with criminal groups or fraud schemes, as well as transactions with other relevant entities, such as exchanges and fiat off-ramps where criminal proceeds are converted to cash.
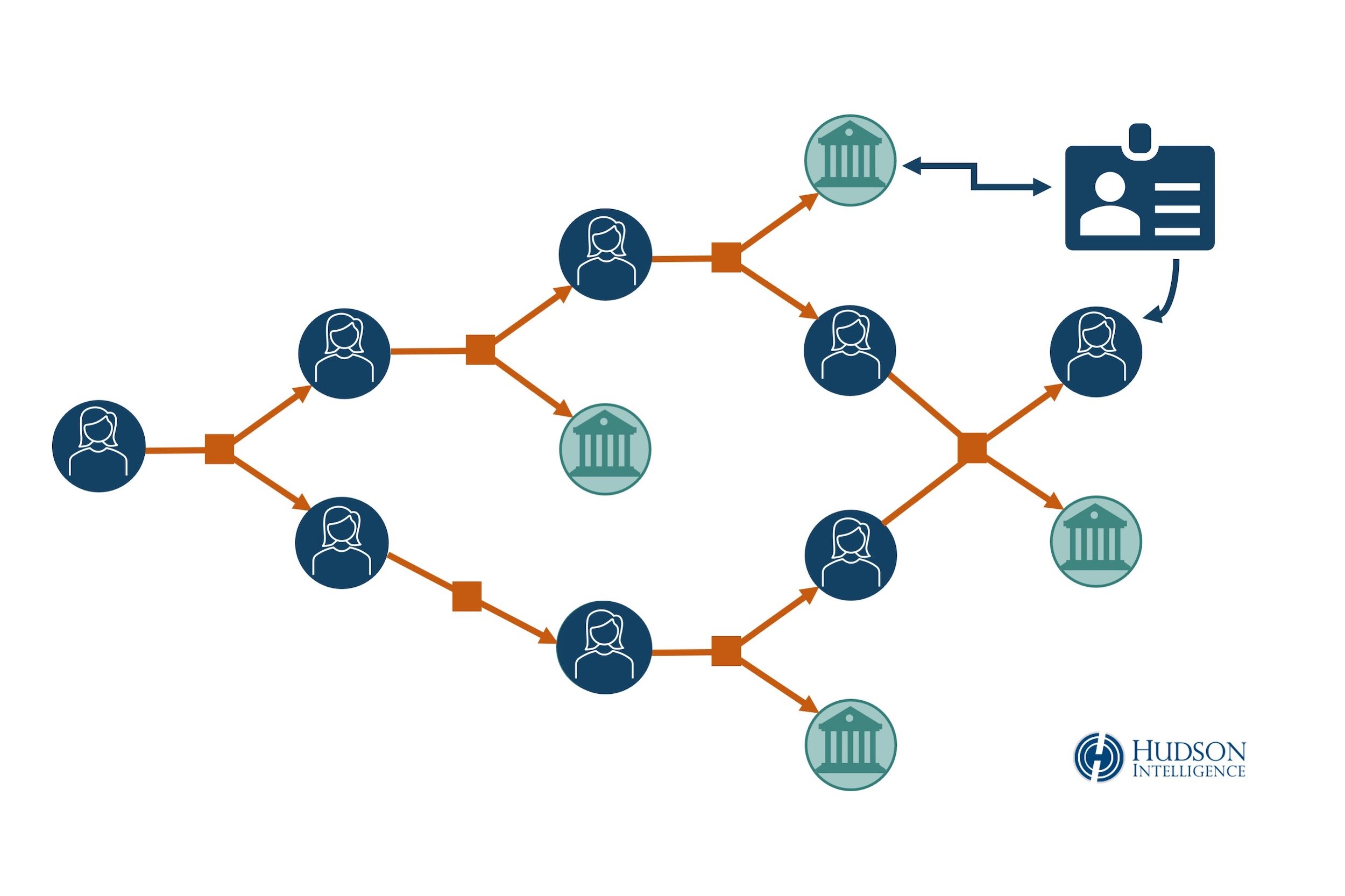
Transaction Mapping: Transactional data is converted into visual maps and flowcharts, showing interactions by the subject with known exchanges and other entities, tracing financial transfers to their ultimate endpoints. Visual mapping makes it much easier to recognize patterns, such as layering and peel chains, commonly used for money laundering. Expert investigators use powerful tools that automate mapping and evidence collection. This approach is more efficient and more effective than blockchain search engines or open-source explorers that require manual review of ledger entries.
Cluster Analysis: A cluster is a group of cryptocurrency addresses that are controlled by the same person or entity. Expanding the focus of an investigation from one address to a larger cluster can dramatically increase the amount of available evidence for de-anonymization and asset tracing. Cluster analysis can also be used to determine if any linked addresses have a substantial current value or UTXO.
Subpoena Targets: Commercial cryptocurrency exchanges, decentralized finance (DeFi) firms, and virtual asset service providers that comply with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations typically require verification of customer identity for new accounts. This makes them a highly valuable resource for de-anonymizing subjects who have used their services to buy, trade, hold, or cash-out cryptocurrency. Personally identifying information for registered owners of addresses and wallets – as well as their banking details – may be obtainable through civil subpoenas or criminal warrants.
Current/Historical Value: Cryptocurrency addresses with significant value are critical indicators for financial recovery. They may be appropriate targets for seizure warrants by criminal prosecutors, or garnishment during civil judgment enforcement.
Total Transactions: Volume of cryptocurrency transactions can signify the potential size of a fraud scheme and number of victims. Complaints to law enforcement typically receive more attention when a crime syndicate has harmed numerous people. Larger schemes may also be appropriate for class action suits in civil court.
Risk Profiling: Automated risk-scoring is conducted through advanced algorithms that trace activity of target address(es) and identify associations with known entities such as exchanges, mixers, peer-to-peer exchanges, sanctioned parties, ransomware rings, and darknet markets.
IP Address: Privacy-piercing metadata is collected through blockchain surveillance systems, which run networks of nodes that “listen” and “sniff” for Internet Protocol (IP) addresses associated with certain transactions. IP addresses, when available, may provide information regarding the geographical location of the subject at the time of the transaction.
Cryptocurrency theft and fraud schemes vary in terms of the technical sophistication of the responsible parties, and the steps they take to conceal their identities. Multiple factors – including the extent of activity in foreign countries or offshore jurisdictions – influence whether the investigation and dispute resolution processes will achieve a positive outcome.
Investigation of complex frauds often benefits from a comprehensive approach that combines blockchain forensics with supplemental, off-chain investigation.
Fraud investigators generally begin by reviewing the narrative of events and timeline of the scheme to gather material evidence of fraud and document the extent of financial losses. Relevant cryptocurrency transactions are traced to determine the disposition of misappropriated funds, including deposits at commercial exchanges. Forensic analysis and blockchain intelligence tools are used to develop attribution data on account owners and identify clusters of interrelated addresses under common control. Investigations may also include digital forensics of email metadata, domain servers, and IP address geolocation.
Other avenues of fact-finding and legal discovery — such as subpoenas in civil litigation, or warrants in criminal prosecutions — may be necessary to positively identify operators of cryptocurrency fraud schemes. Hudson’s investigators provide logistical support to legal counsel, including vetting of appropriate subpoena targets (e.g., KYC-compliant exchanges) and examination of bank records and related materials obtained under subpoena. For class action lawsuits, it may be appropriate to identify and interview other victims for inclusion as class members.
Once the principals have been positively identified, due diligence may be conducted to develop relevant information on their backgrounds, including investigation of criminal history, professional credentials, financial liabilities, and any pattern of involvement with past frauds. Such research may include acquisition and review of business records, court filings, and financial records. If the scheme originated outside the United States, it may be necessary to coordinate these efforts with local sources overseas.
Hudson’s investigators assist clients in preparing formal criminal complaints and coordinating with law enforcement agencies in the U.S. and foreign jurisdictions.
Consult an Investigator
Hudson Intelligence assists law firms, businesses, public agencies and investors with cryptocurrency tracing, fraud investigation, and due diligence. Every investigation is led by a Cryptocurrency Tracing Certified Examiner (CTCE) and Certified Fraud Examiner (CFE). If you would like to discuss a potential investigation, please complete the form below. We also suggest reviewing our FAQ.